
New research shows how young people are encountering requests for sexual exchanges at concerning rates—at times involving offers of money or other items of value in exchange.
For trust and safety teams, this represents a need to revisit thinking about the existing frameworks of sexual exploitation of children and commercial marketplaces for child sexual abuse material (CSAM) and develop additional mitigations. Risk dynamics are shifting, expanding the profile and tactics of the “buyer” in these exchanges while also illustrating new situations where a potential victim may be less likely to report an abusive interaction.
At Thorn, we know these types of exploitation are hard to moderate. Our latest research, Commodified Sexual Interactions Involving Minors: New data on evolving dynamics in technology-facilitated child exploitation, sheds light on the underlying prevalence of sexual solicitations minors are confronting online alongside an emerging range of commodified interactions involving money, social capital, and other items of value.
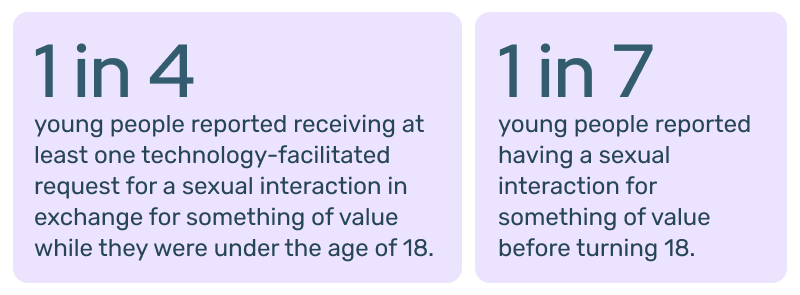
The study shows that 1 in 4 young people report receiving a solicitation to exchange sexual imagery, engage in sexual talk, or participate in a sexual interaction in return for something of value before turning 18.
The Changing Landscape of Child Sexual Exploitation
The study, which surveyed 1,200 young people (ages 13-20), found that the standard perception of adults over 25 preying on minors is not always the reality for many young people.
Who’s buying? Breaking down commodified sexual interactions with a minor:
- 1 in 4 (25%) young people reported being asked to provide sexual content or engage in sexual activity in exchange for something of value.
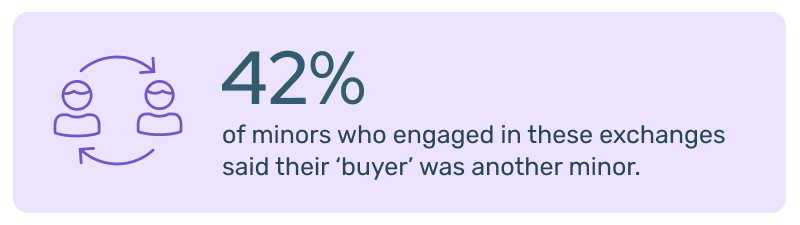
- 42% of minors who engaged in these exchanges said their ‘buyer’ was another minor.
- 65% said their buyer was an adult.
Money was the leading form of compensation in these exchanges; however, new research reveals that social and digital incentives—such as increased online followers, exclusive social opportunities, and gaming currency—also significantly shape these harmful exchanges.
How the currency of sexual exploitation is changing:
15% of young people reported engaging in at least one such transactional sexual experience as a minor. Among those who engaged in these exchanges:
- 58% received money
- 33% received social opportunities (e.g., party invitations, more followers online)
- 28% received material goods like clothing, beauty products
- 9% received gaming currency
Why This Matters
As digital spaces evolve, these transactions are fueled by the unique value of today’s online communities. The increased normalization of transactional interactions in digital environments creates new and often overlooked pathways to exploitation.
This collision of two normal behaviors, identity exploration and commercial transactions, creates an environment where traditional social capital (status, popularity) has transformed into quantifiable digital metrics (followers, likes). This produces new risks when sexual content becomes a means of digital social currency with real or perceived value.
"Digital spaces weren't built with the social development needs of young people in mind, yet today's teens navigate their formative years in these environments," said Melissa Stroebel, VP of Research and Insights at Thorn. "Without traditional interpersonal cues and faced with new incentive dynamics, young people are building relationships and taking risks in fundamentally different ways. We need to speak more candidly about what this means—how digital social currency and validation can lead to unintended outcomes—and equip them with skills to navigate these moments safely. Understanding these dynamics is crucial for building effective safeguards that respect their agency while reducing potential harm."

What Trust and Safety Teams Can Do
These emerging dynamics present unique challenges for detection and intervention within the platforms where they occur. Many current moderation and safety tools rely heavily on user reporting to identify violative interactions and enforce policies. However, the dynamics identified in this report point to interactions minor victims may have less motivation or incentive to report.
In the face of these challenges, platforms should:
- Proactively evaluate how their features, ecosystems, and engagement models may facilitate and sustain these illicit exchanges.
- Integrate a demand-side disruption approach by analyzing data from suspended or deplatformed accounts that have been known to engage in these exchanges.
- Identify consistent behavioral signals, detect multi-account linkages and coordinated behaviors, and map network and engagement patterns.
- Strengthen cross-platform collaboration by sharing case studies, detection strategies, and emerging patterns of abuse.
Prevention strategies must reflect the complexity of young people's experiences, addressing explicit threats and the more subtle, normalized risks embedded in digital environments. By understanding the nuance of young people’s identity exploration online, we can adapt safeguards that not only support them in exercising their agency but also reduce the likelihood that they will come to harm.
Learn more about mitigating child safety risks:
- Read the report to get details on young people’s experience with transactional sexual solicitation online.
- Explore our blog series on what digital platforms need to know about child sexual abuse material.

